Free vector Risk assessment flowchart for cyber security management Security cyber network tips cybersecurity computer steps infographic diagram degrees diagrams conceptdraw example networks solutions architecture solution information risks threats
Cyber Security Threats and Data Flow Diagrams
Incident cyber response template plan structure immediately planning usable guidance Security network diagram model cloud diagrams government computer solution devices conceptdraw example access networks architecture solutions cybersecurity information models examples Cybersecurity policies & procedures
Rfid vm
Cyber security framework mind map templateCyber security diagram Cyber security incident response process flow chart deploying computerArchitecture cybersecurity enterprise iot cyber security diagram system software.
Crime evidence ipcCybersecurity and digital business risk management flow diagram of Data flow diagram in software engineeringProcess flow vs. data flow diagrams for threat modeling (2023).

Cyber security flow chart
Cybersecurity incident response plan template and example ukCyber security isometric flowchart royalty free vector image Data flow diagram of smart security frameworkNetwork security.
Cyber security threats and data flow diagramsCyber security flow chart Cyber incident flow chartFlow chart on cyber security from research paper.

Cyber security flow chart
Data flow diagramCyber security: a paradigm shift in it auditing Nist cybersecurity frameworkCyber security flowchart royalty free vector image.
Data flow and security overviewSecurity flow cyber data event logging diagram logs internet important why so together putting events au Flow cybersecurity chartCyber security compromise flow chart.

Cyber security flowchart
Iot & enterprise cybersecuritySecurity event logging, why it is so important – aykira internet solutions Rfid vm security system flow chartNetwork security tips.
Network security modelNetwork security model Security network diagram control computer diagrams devices networks secure access encryption solution cloud examples model architecture example conceptdraw software systemFlow chart cyber security compromise australia.

Flow chart of cyber investigation : cyber crime awareness society
Security conceptdraw firewall firewalls architectures infrastructure networking systems lan devices create wan protecting realtek privacyCyber security incident response process flowchart ppt powerpoint Cybersecurity procedures implementation yokogawa customer developing implement solutions benefits accordance practices.
.


Cyber Security Diagram | EdrawMax Template

Risk Assessment Flowchart For Cyber Security Management
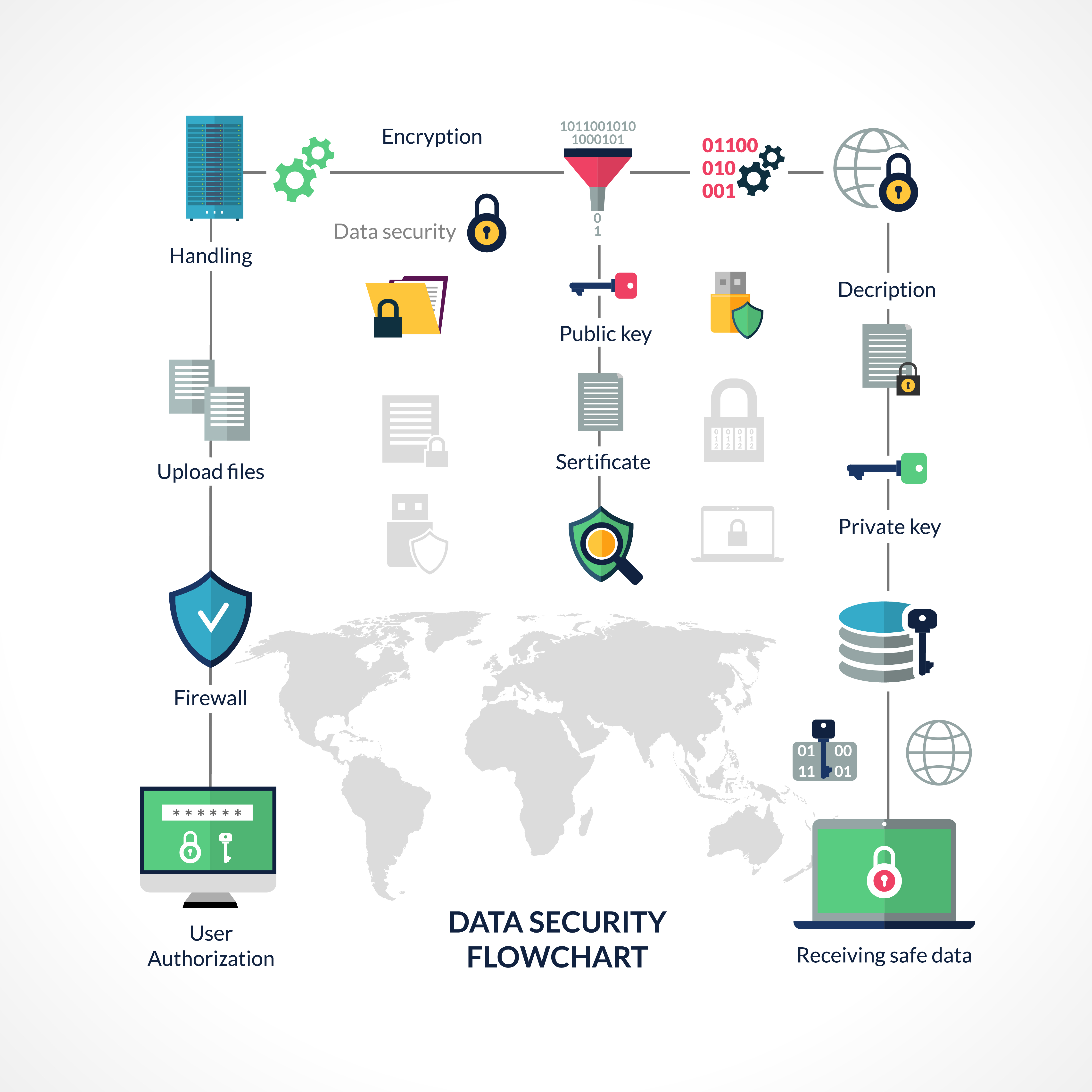
Cyber Security Flowchart

Cyber Security Threats and Data Flow Diagrams

Network Security Model

Security Event Logging, why it is so important – Aykira Internet Solutions

Data flow diagram of smart security framework | Download Scientific Diagram